What is an EDI protocol ?
12 June 2023
12 June 2023

The digital transformation of companies is increasing internal digital data flows and inter-company data exchanges. To achieve this, EDI solutions use data exchange protocols. But what is an Electronic Data Interchange (EDI) protocol ?
In this article, find out :
Electronic Data Interchange is the electronic exchange of documents between a company and its trading partners.
All EDI and data integration solutions, such as EAI and ETL, use data exchange protocols that govern the modes and rules of information transmission.
These protocols make it possible to :
For two systems, a sender (client) and a receiver (server), to work together by exchanging messages, it is necessary :
A data exchange protocol (EDI) enables this last point to be satisfied. It dictates the rules of communication between the two systems, client and server, and contains a specification of the various rules and procedures to be followed for transmitting and receiving data, and the language codes enabling communication.
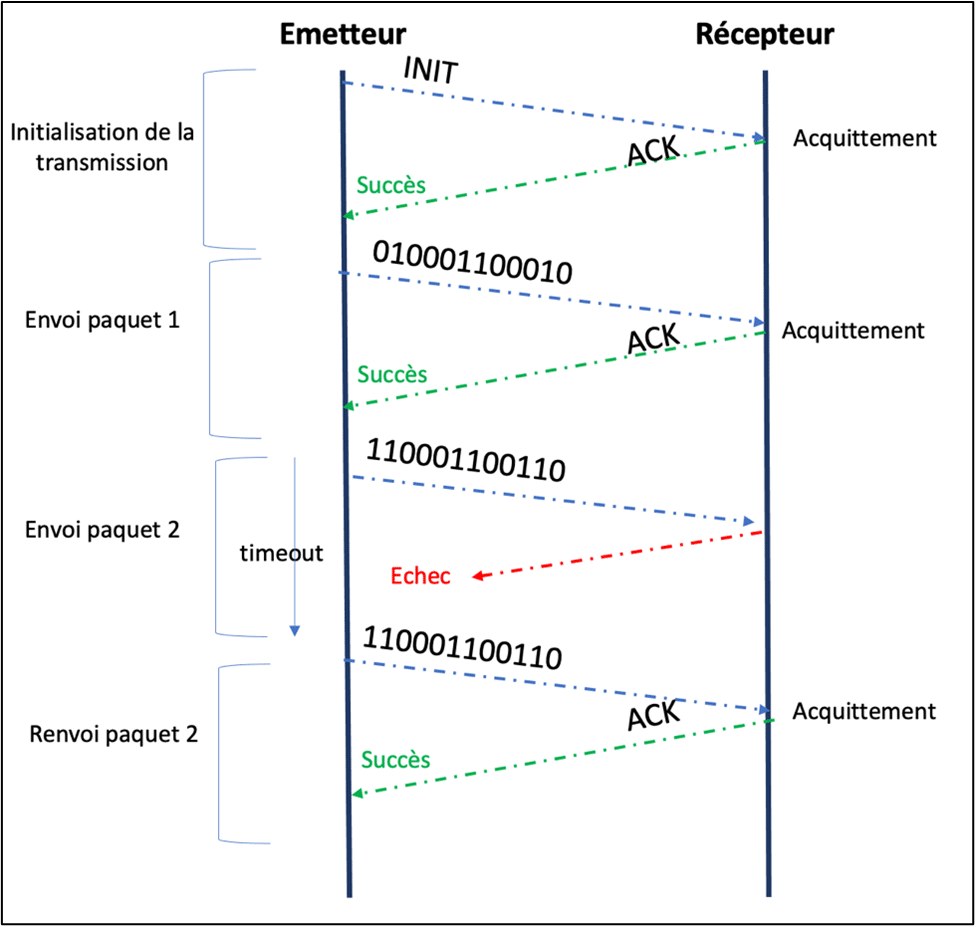
The method used to guarantee a successful data transfer between a sender and a receiver is to return an acknowledgement of receipt, and to send the data again if the acknowledgement does not arrive within the time allowed for acknowledgment.
A data exchange protocol handles all types of data, whatever the format of the messages exchanged. The protocol is a set of formal rules governing :
Data is transmitted in packets between sender and receiver.
The role of the protocol is :
To achieve this, the protocol adds additional information, such as sequence numbers and control elements, to the individual packets transmitted. This information enables the receiving system to check the quality of the data received and to rearrange them in order to reconstitute the message received. It returns an acknowledgement or an error code defined by the protocol to signify “ok” or “transmission failure”.
What’s more, to secure transmissions and protect them from accidental or deliberate data leaks, many protocols add security measures such as authentication and encryption procedures.
To sum up, data exchange protocols enable you to :
Choosing the right data exchange protocol (EDI) means taking into account technical and business environments. Here are the main protocols and methods used in EDI and data integration solutions.
FTP, File Transfer Protocol, is the native file exchange protocol on TCP/IP networks. Easy to use, it is no longer recommended due to its security weaknesses. However, it is still used internally for manual file transfers, as it is an easy-to-use TCP/IP standard.
File Transfer Protocol Secure is a version of FTP. FTP/S supports TLS (Transport Layer Security) and SSL (Secure Sockets Layer) encryption. This makes FTP transfers secure.
Secure File Transfer Protocol uses FTP and SSH, Secure Shell. SSH is used to establish a secure connection tunnel between the client and the server, through which FTP flows. SFTP is recommended to replace FTP for file and EDI message exchanges.

HyperText Transfer Protocol is used primarily for sending and receiving web pages. HHP/S supports SSL/TLS to secure and encrypt Internet transactions.
AS for Applicability Statement, AS2 and AS4 are two protocols used for data exchange over the public Internet.
They are used for EDI transactions. Their advantage is that they enable fast, reliable connections to be established without the need for VAN networks, which are often too costly to use.
But AS2 requires security procedures on both sides to isolate AS2 access: authentication, firewall, DMZ, etc. Unlike AS4, which operates on a push/pull basis, it requires a permanent connection from the EDI message recipient.
AS4 is an evolution of AS2, developed on the basis of Web Services for ebXML messaging services. AS4 features notification and security capabilities, WS-Security, which are absent from AS2.
Odette File Transfer Protocol version 2.0 is the latest version of OFTP.
Odette, Organisation for Data Exchange by Tele Transmission in Europe, is the originator of the OFTP protocol. In France, Odette is represented by Galia, Groupement pour l’Amélioration des Liaisons dans l’Industrie Automobile. OFTP2 enables EDI transactions over the public Internet, offering encryption, data compression and support for large files.
APIs, Application Programming Interfaces, are programming interfaces that connect :
APIs enable interaction and data exchange.
The advantage of APIs is their real-time nature. They can synchronize data, query databases and return status information.
There are two main categories of API :
Today, APIs are used in a wide variety of ways :
Tenor has been an expert in data flow exchange for over 30 years, supporting you in your data management, EDI and e-invoicing projects.